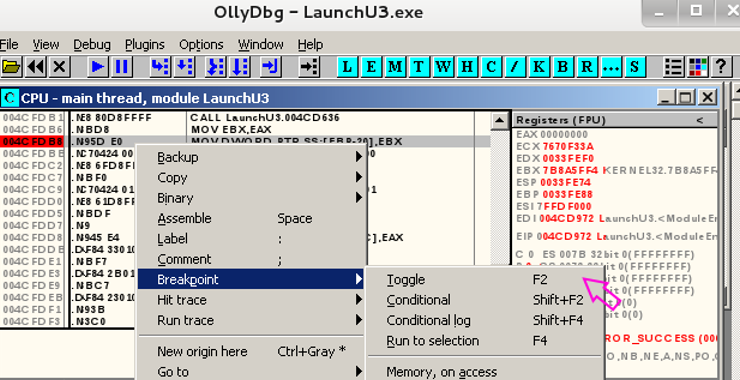
Reverse Engineering Malware, Part 5: OllyDbg Basics
In this series, we are examining how to reverse engineer malware to understand how it works and possibly re-purposing it. Hackers and espionage agencies such as the CIA and NSA, regularly re-purpose malware for other purpose. Previously, we looked at the basics of IDA Pro, the most widely used disassembler in our industry. In this […]
Continue Reading