Reverse Engineering Malware, Part 2: Assembler Language Basics
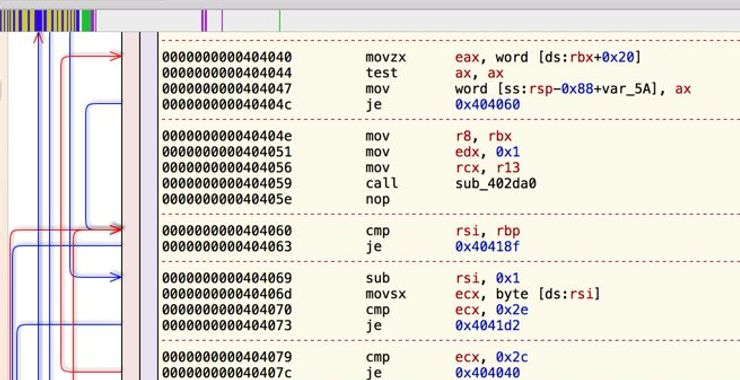
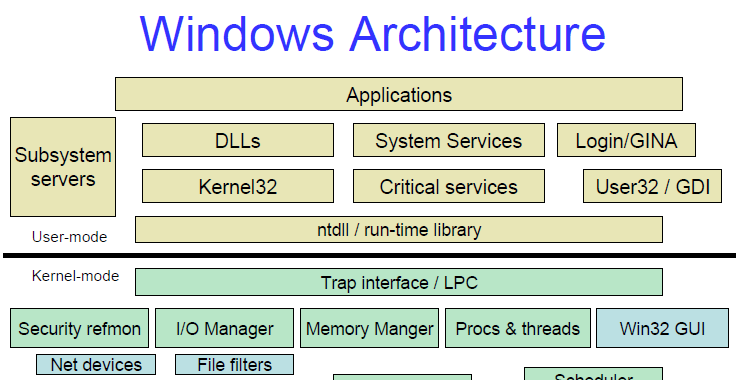
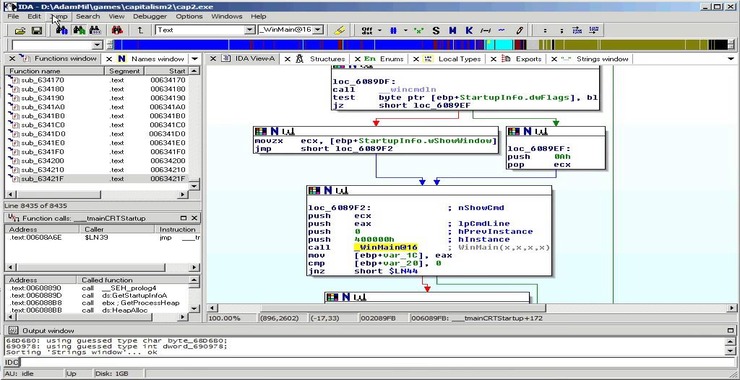
Most of the work we will be doing in reverse engineering will be with assembler language. This simple and sometimes tedious language can reveal a plethora of information on the source code. When we can’t see or recover the source code of the malware or other software, we can use tools such as dis-assemblers and […]
Continue Reading