Network Forensics, Part 1
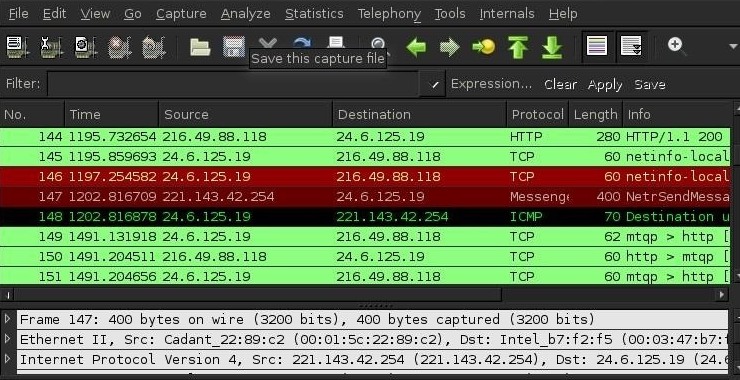
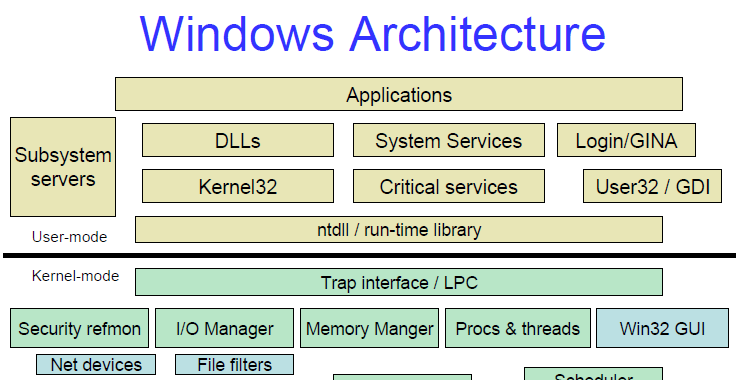
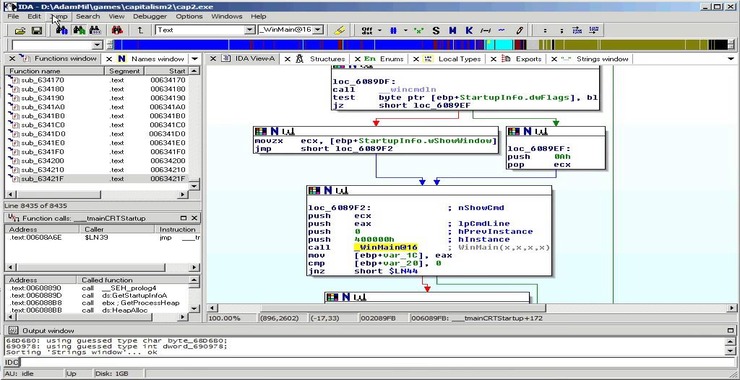
Welcome back, my hacker apprentices! Network forensics is key element of most digital forensics and incident response (DFIR) investigations. When our systems have been compromised by an attacker, its up the DFIR investigator to determine the who, what, where and how of the attack. In other words, what can a DFIR investigator learn about the […]
Continue Reading