Exploit Development: Fuzzing with American Fuzzy Lop++ (AFL++) to Find Zero-Day Vulnerabilities
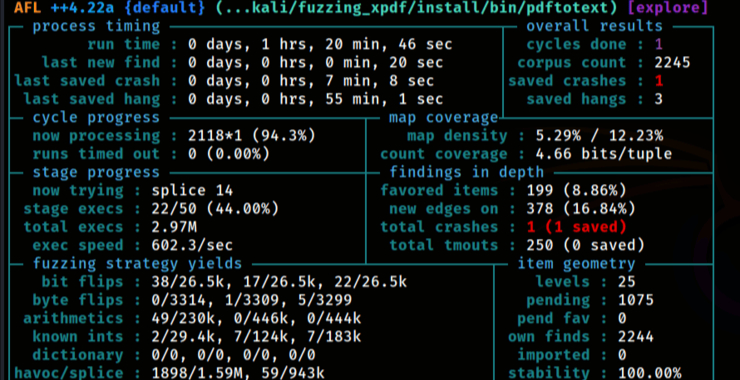
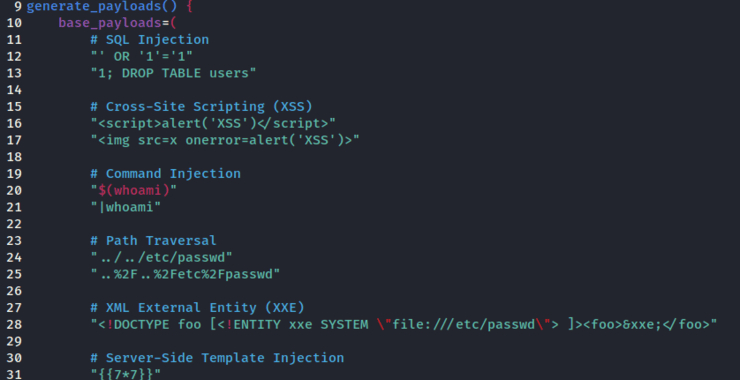
Welcome back, my aspiring cyberwarriors! Finding vulnerabilities in applications and services is the first step toward developing your own zero-day exploit. Vulnerability scanners are great for finding KNOWN vulnerabilities, but to find unknown or zero-day vulnerabilities a fuzzer is an excellent tool that you should be familiar with. As you know, fuzzing is the […]
Continue Reading