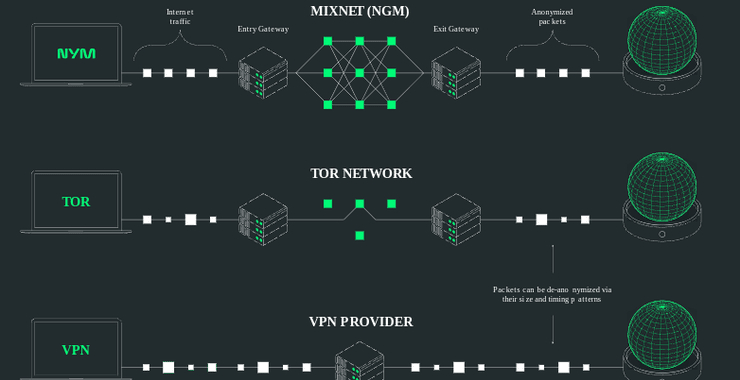
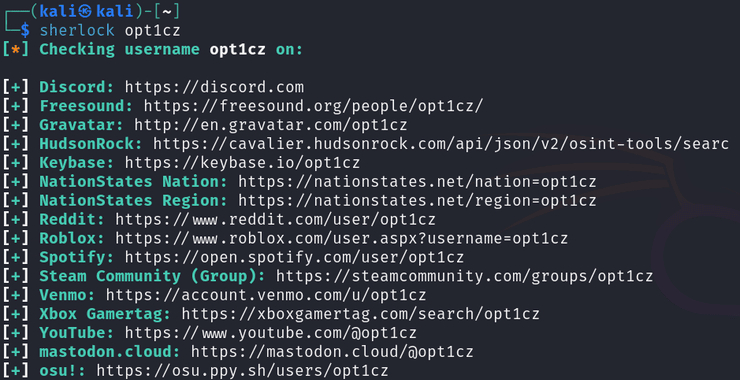
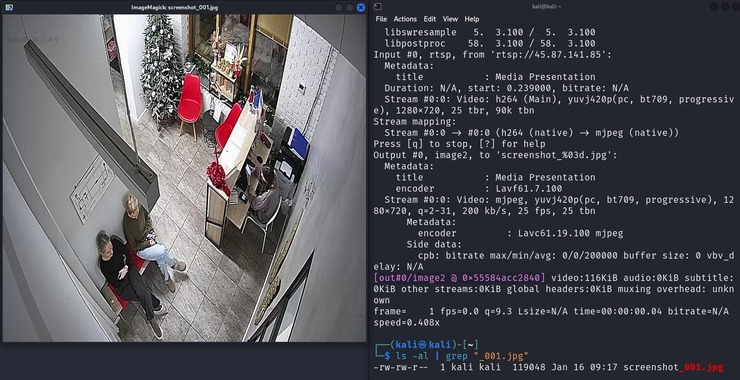
Ukraine/Russia Cyber War! Using SQLi Against Russian Websites, Part 2
Hello cyberwarriors! This is Overwatch from Ukraine again! In the first segment of this series, we walked through different modifications of SQLMap payloads. Today, we’re continuing our SQL injection series, but will focus on automating the scanning process to save time and make it easier to work with larger sets of websites. We’ll use a […]
Continue Reading