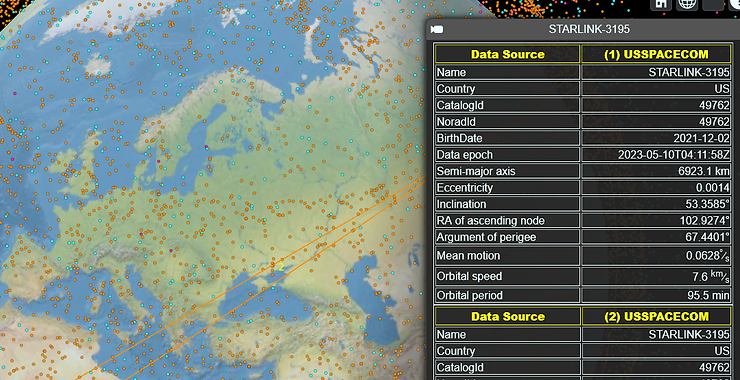
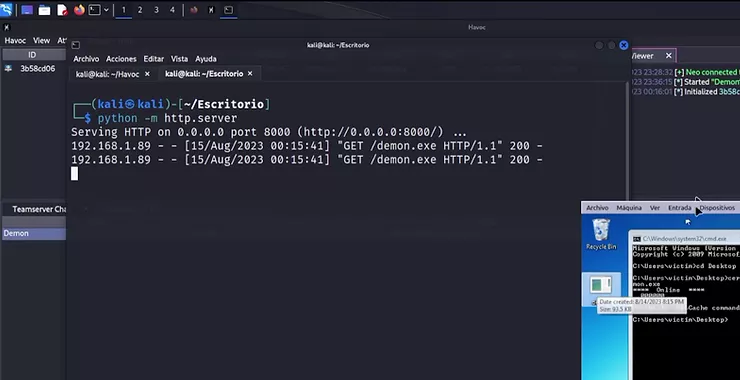
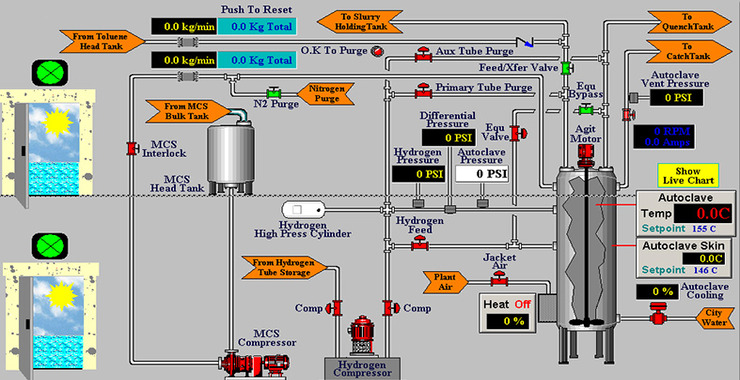
Cyberwar Mission #3: Using QRCodes in Phishing and Social Media Attacks
Welcome back, aspiring cyberwarriors. In this article, one of our fighters in Ukraine (Sierra) demonstrates how they use social engineering to turn Russian tactics against them. In each new article here, we delve into the cyberwarrior wisdom of Master OTW and its application in cyber warfare. In this edition, I will discuss Master […]
Continue Reading