Metasploit Basics, Part 5: Using Metasploit for Reconnaissance (nmap, EternalBlue, SCADA, and MS SQL)
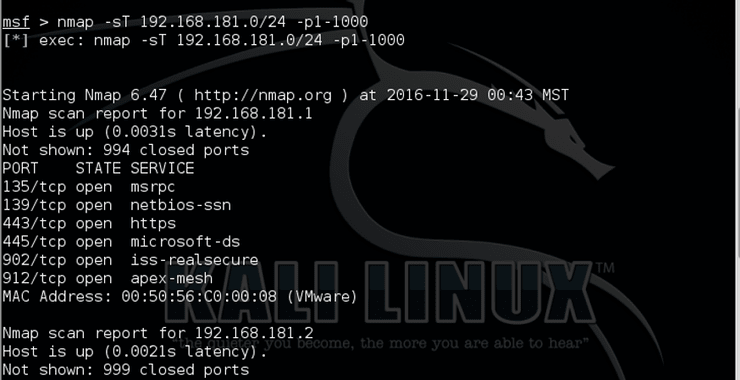
Welcome back, my rookie hackers! As you know, reconnaissance is a crucial part of the hacker/pentester’s job. Without good reconnaissance, it is likely that all your work and effort will go for naught. As Metasploit has evolved from strictly an exploitation framework to a multi-faceted, penetration testing tool, it has added additional capabilities, including reconnaissance. […]
Continue Reading