Metasploit Basics, Part 22: Exploiting and Controlling a System When You Have Physical Access
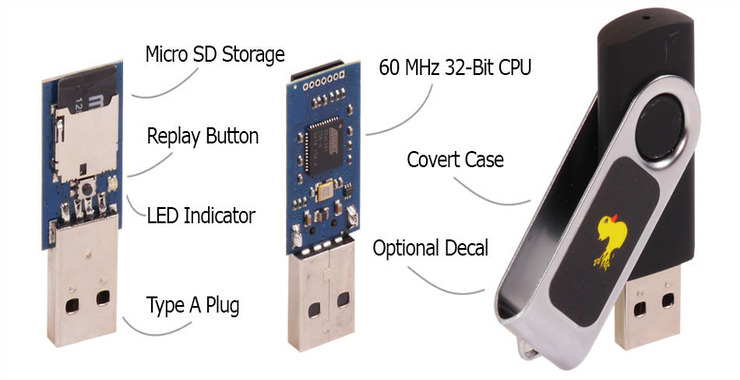
Welcome back, my aspiring cyber warriors! Much of what we have done here in this Metasploit Basics series enables us to exploit and control a remote system anywhere on the planet earth (or at least any machine connected to the Internet on planet earth). In some cases, we may want to control a system that […]
Continue Reading