SCADA Hacking: Finding Specific SCADA Systems with Censys
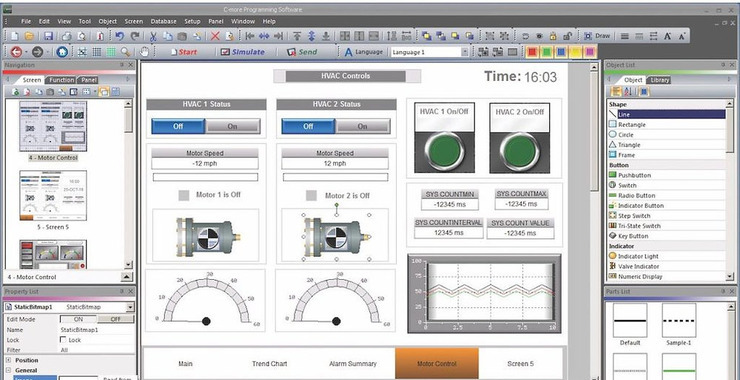
Welcome back, my aspiring SCADA Security Engineer! As you know, SCADA/ICS systems around the world are under attack. These systems are industrial systems that make up the infrastructure of any nation’s economy and are the prime targets in any cyberwar. In such a war, these systems can be easily found via a variety of tools […]
Continue Reading