SCADA Hacking: Attacking SCADA/ICS Systems through the Human Machine Interface (HMI)
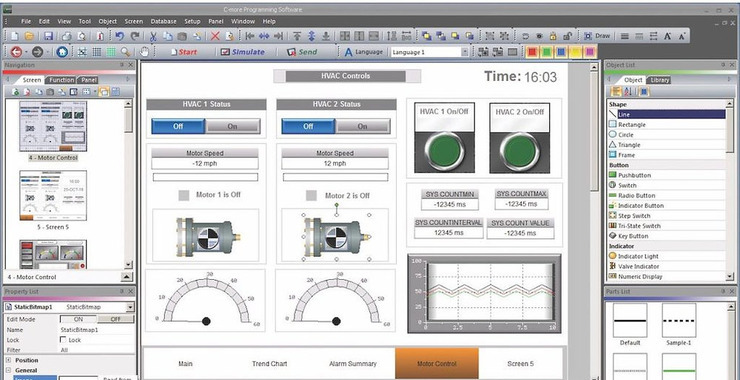
Welcome back, my aspiring SCADA/ICS cyberwarriors! Let’s begin by congratulating you on your foresight in committing to study SCADA/ICS hacking and security. This is certainly THE most important security issue this decade! In general, SCADA/ICS hacks have been of two types; Hack the protocols (modbus, DNP3, Profitnet, etc); Hack the Human Machine Interface (HMI) In […]
Continue Reading