Database Hacking, Part 3: Using sqlmap for SQL Injection Against MySQL and WordPress
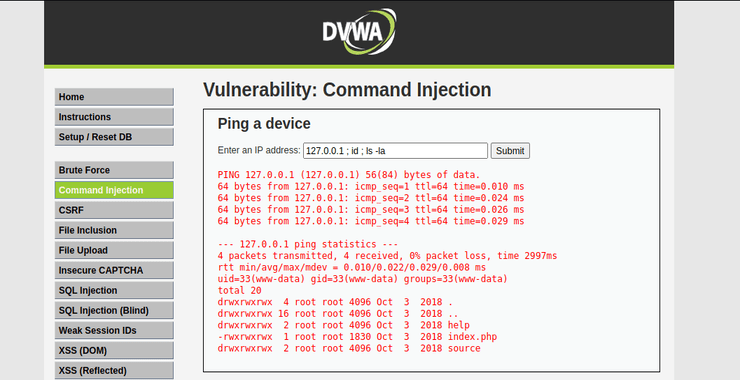
SQL Injection is one of the most important and common attacks on web sites. Nearly every website has a database behind it containing confidential and valuable information that can often be compromised by a well-designed SQL injection attack. There are many SQL injection tools, but probably the most popular is sqlmap. In this tutorial, we […]
Continue Reading