The CyberWarrior Handbook, Part 1
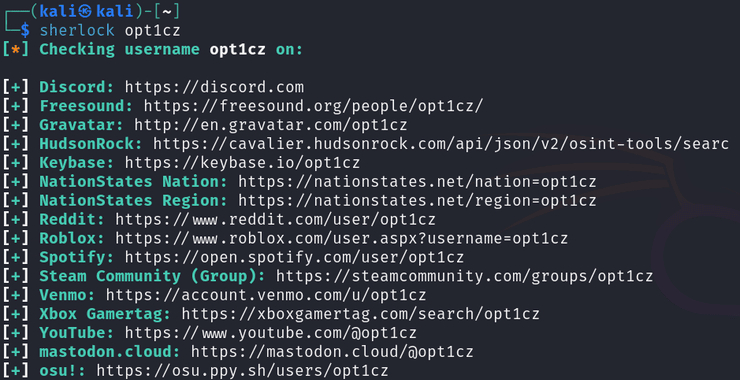
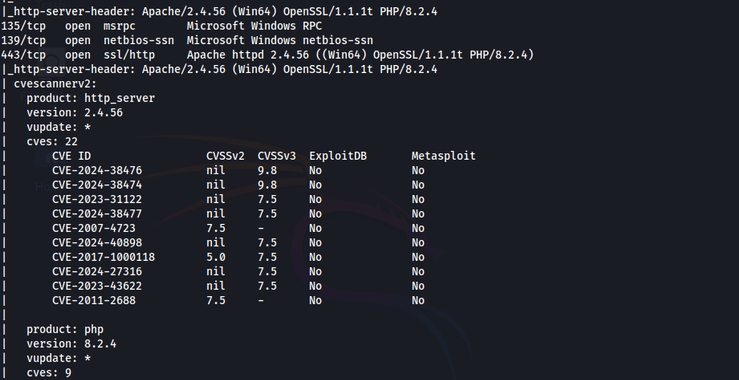
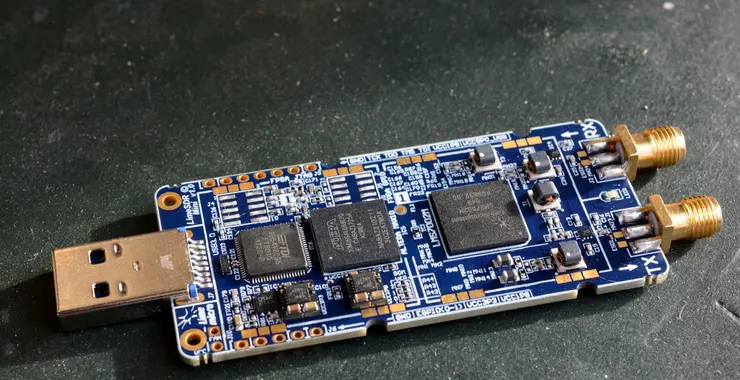
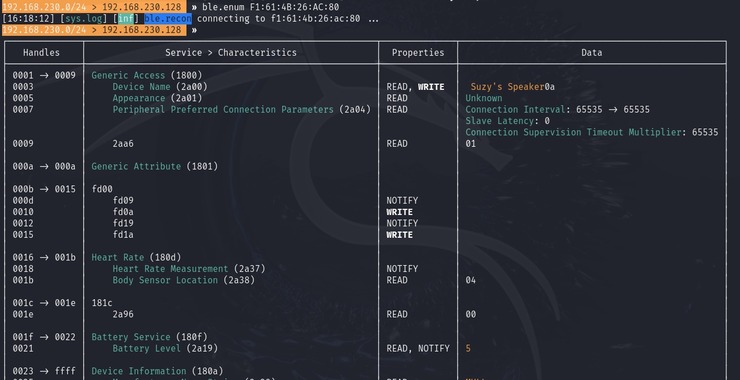
Welcome back, my cyberwarriors! In this series, we will detail how an individual or small group of cyberwarriors can impact global geopolitics. The knowledge and tools that YOU hold are a superpower that can change history. Use it wisely. To begin this discussion, let’s look at the actions of a small […]
Continue Reading