Satellite Hacking, Part 1: Getting Started
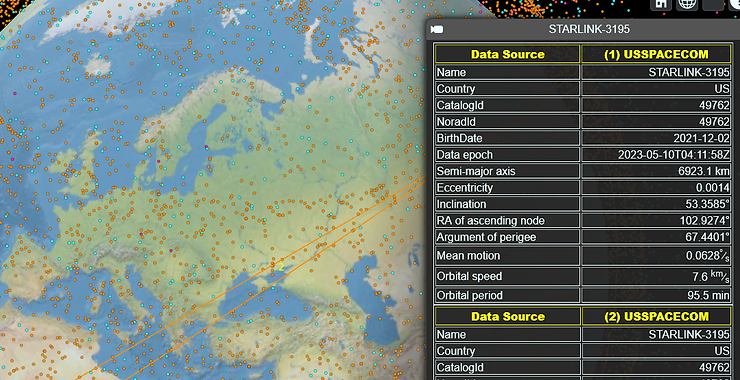
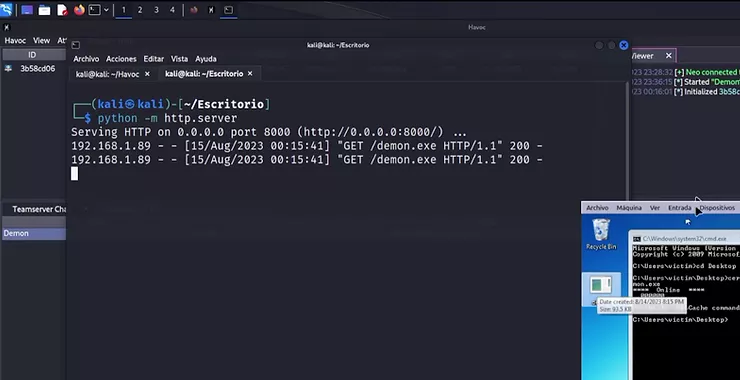
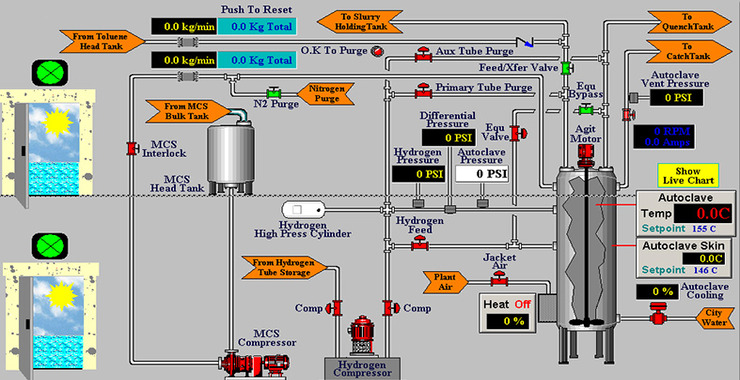
Welcome back, my aspiring radio satellite hackers! In this series of tutorials, we will be exploring hacking satellites from a multitude of approaches. Satellites have become a ubiquitous and necessary technology in our everyday lives. They provide us with internet access, television and radio signals, location services, satellite phone service and, of course, satellite images […]
Continue Reading