Open Source Intelligence (OSINT): Finding Breached Email Addresses , Passwords and Other Credentials
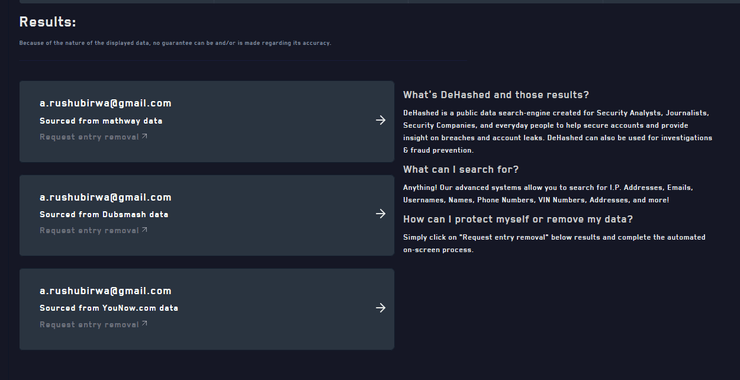
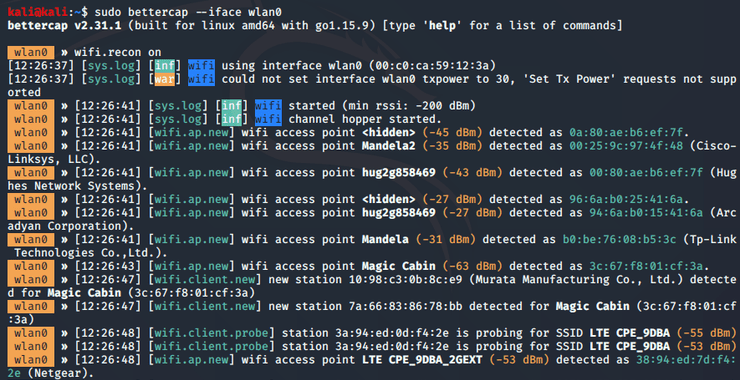
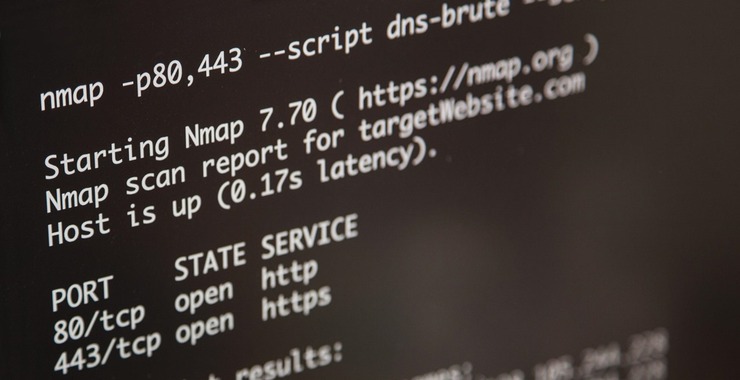
Welcome back, my aspiring OSINT Investigators! In the course of OSINT or forensic investigations, there are often times when you will need an email password of the subject of your investigation. In a security assessment or pentest, you may want to check to see whether you can obtain the passwords of users in the target […]
Continue Reading