The Return of the Devastating DDoS Attacks or The Revenge of the IoT
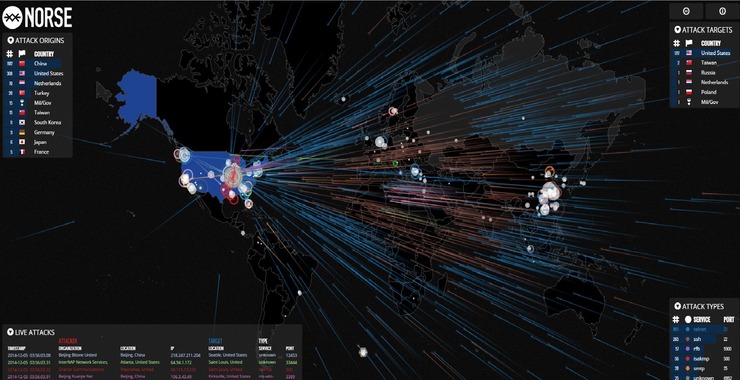
Welcome back, my aspiring cyberwarriors! As you well know, the Distributed Denial of Service (DDoS) attack is one of simplest attacks. It is simply brute-force packet jamming a network to render it useless or nearly useless. When its done with just a few nodes it can be easily thwarted by a number techniques such as […]
Continue Reading