SCADA Hacking: Metasploit SCADA Modules
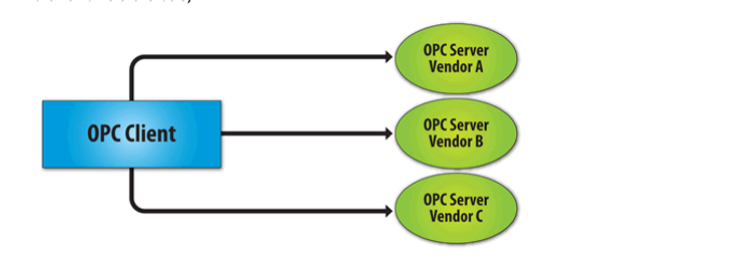
As a penetration tester/hacker, we have many resources we can use to test SCADA/ICS system security. One of the most popular is the Metasploit Framework. Here, I have tried to compile a list of most of the Metasploit modules that are useful for testing/hacking SCADA/ICS. Please keep in mind that SCADA/ICS sites use varied hardware […]
Continue Reading