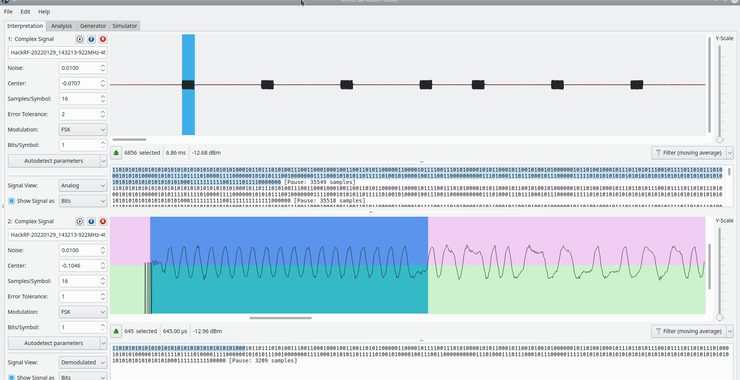
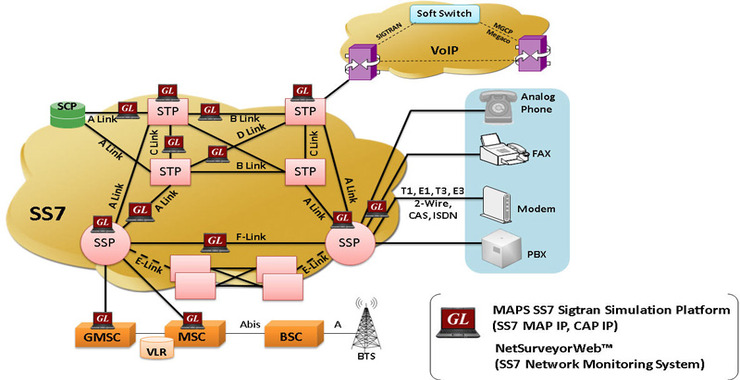
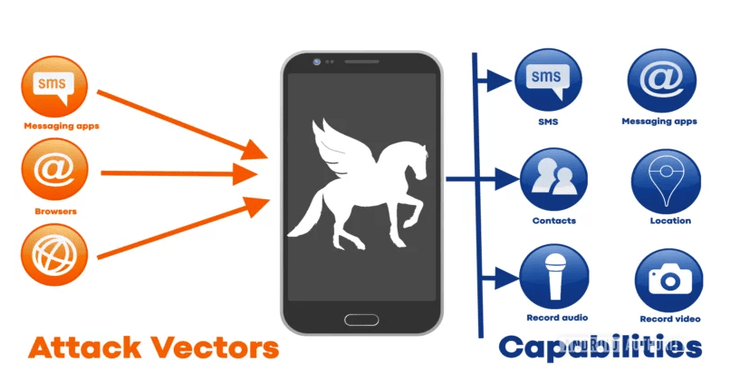
SDR (Signals Intelligence) for Hackers: Soon, all Cellphones will be Connected by Satellites
Welcome back, my aspiring cyberwarriors! In earlier posts here, we have described hacking satellite communication systems. While many might see that type of hacking as very advanced and maybe a bit esoteric, new technologies are about to make satellite communication ubiquitous for everyone with a cellphone. We are on the cusp on an era […]
Continue Reading