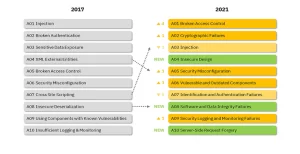
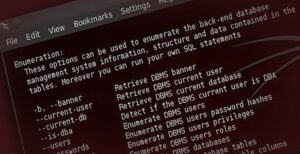
Database hacking is among the most important arts of the hacker. Usually, the hacker is seeking access to data and obviously, the database is usually where it resides. This makes the database the “Golden Fleece” of the hacker.
Most often, databases are hacked using SQL injection and as such, this section will focus on SQL Injection (SQLi) techniques and tools.
Start by reading these articles on databases.
Learn more in the courses: