Gaining access to the target’s system can be more complex than simply running an exploit against the system. Usually, you can expect that the target system has some type of anti-virus protection (your payload is a virus). To be successful then, you must find a way to evade the anti-virus software. This section is dedicated to finding ways to get your shellcode/payload past detection of the target’s AV software.
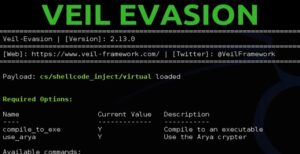
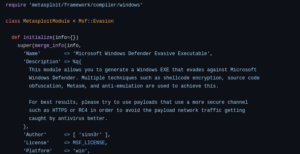
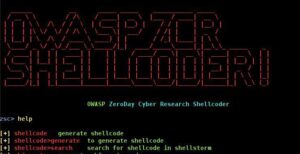
Most AV software uses signature detection, so you only need to change the file signature of the payload to get it past the AV detection. There are several tools available for this including; Veil-Evasion, Shellter, Sharpshooter, Metasploit Evasion modules, and OWASP-ZSC, among others.
When trying to evade detection by the target’s AV, you don’t need to evade ALL AV software, but rather just the AV software being used by the target. You can detect which AV software the target is using by running recon-ng.
To create payloads that are undetectable to AV, try any of these tools and techniques.
Learn more in the courses: