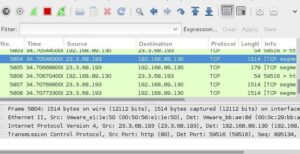
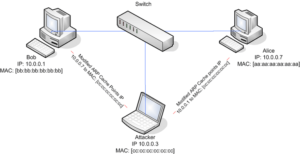
Man-in-the-Middle Attacks are among the most nefarious attacks. In these attacks, the hacker places themselves between the client and server. In this way, the attacker can eavesdrop or even alter the communication between the end points. Imagine someone reading all your email and other communication and even worse, intercepting it and altering it.
Learn more in the courses: