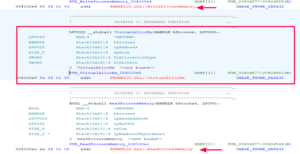
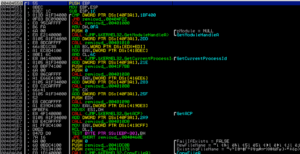
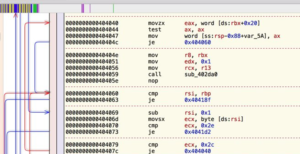
In this series, we will examine how to reverse engineer malware. Like so many skills in information security, these skills can be used by both Black and White Hats. White Hats use to it understand how the malware works to defeat it and to assign attribution; the Black Hats use it to reverse engineer a known piece of malware to give it additional capabilities and avoid detection. Whatever you do, this is a very high-level skill-set that is great demand within our industry. It is probably the highest paid sub-discipline within information security.
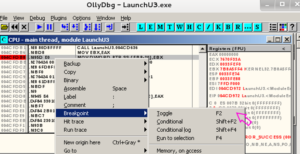
I will attempt walk you slowly through the knowledge base and skill sets you will need to reverse malware. These include a basic knowledge of assembler and C, how to use such tools as IDA Pro, Immunity and Ollydbg, basics of Windows and Linux operating system structure and function and then finally, how to edit to code to add functionality and stealth.
Learn more in the courses: