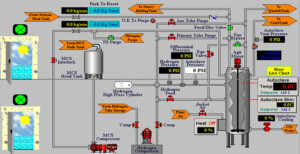
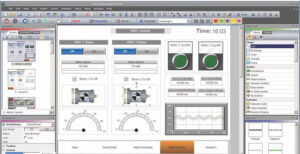
SCADA/ICS systems are among the greatest concerns for cyber warfare/cyber defense organizations. These systems are particularly vulnerable for several reasons, including– but not limited to–the fact that so many SCADA/ICS organizations have relied upon security through obscurity for so many years. These industrial control systems are critical to any nation’s infrastructure and, thereby, their economy. In this section, we will be showing how these systems can be found, hacked, and controlled.
Like any type of hacking, we need to do reconnaissance first. You can’t hack what you don’t see. We’ll start with a few tutorials on how to find SCADA/ICS systems with Shodan, Google hacking, and Nmap. Then, we will progress to;
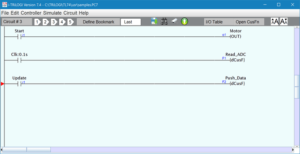
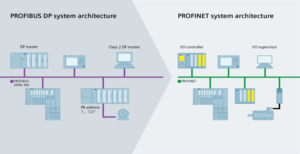
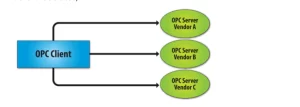
(1) the basics of how these systems work including their primary protocols (Modbus, DNP3, ProfiBus, OPC, etc).
(2) a few case studies of major SCADA/ICS hacks.
(3) and finally, how to hack and exploit them.
For more information on Metasploit, check out these tutorials.