HACKERS ARISE
Expert-led training in cybersecurity tools and techniques, designed for IT specialists, ethical hackers, security engineers, and students.
We operate on two parallel websites Hackers-Arise.com & Hackers-Arise.net
Live and immersive approach to training ethical hackers
Our instructors are experienced pentesters, forensic investigators, and former college professors. They have trained hackers globally across the multiple military and intelligence agencies. With their broad practical expertise they provide students with practical, high-level skills to tackle the complexities of ethical hacking and excel in the field of cybersecurity.

Top Hacking Articles
CyberWar: The Breach at Avtodor – Inside a Russian Government Infrastructure Network, Part 1
NymVPN Setup & Testing: A Hands-On Walkthrough
Database Hacking: SQLite Essentials and Attack Strategies
Socat: The Advanced Hacker’s Network Tool
SCADA/ICS Hacking and Security: Chinese APT, Volt Typhoon, Has Compromised Numerous Industrial Systems in the US!
OSINT: Automatic Collection Of All Available Information With Intelligence X
Physical Security: Hacking Elevators to Gain Physical Access

HACKING ARTICLES
CATEGORIES
- AI
- Anti-Forensics
- Bitcoin
- Bluetooth
- Bug Bounty
- Cellphones
- Cryptocurrency
- Cryptography Basics
- Cyber Threat Intelligence
- Cybersecurity
- Cyberwar
- Cyberwarrior
- Data Analytics
- Data Dumps
- Defensive Security
- Digital Forensics
- DoS
- Email Dumps
- Exploit Development
- FemtoCell
- GPS
- Hacking
- ICS
- InfoSec
- IoT
- IoT Hacking
- Linux
- Lock Picking
- Malware
- Metasploit
- Network Basics
- Offesnsive Security
- OSINT
- ParamSpider
- Pentesting
- Physical Security
- Python
- Ransomware
- Satellite Hacking
- SCADA Hacking
- Scanner
- Scapy
- Scripting for Hackers
- SDR
- Signals Intelligence
- Spidering
- Stingray
- Ukraine
- Uncategorized
- Vulnerabilities
- White Hat
- Windows

Socat: The Advanced Hacker’s Network Tool
Welcome back, my aspiring cyberwarriors! In the world of cybersecurity, certain tools become legendary not because they’re flashy, but because they’re incredibly powerful when used correctly. Socat is one such tool, serving as an advanced version of Netcat. The name stands for “Socket CAT,” and while it might seem intimidating

SCADA/ICS Hacking and Security: Chinese APT, Volt Typhoon, Has Compromised Numerous Industrial Systems in the US!
Welcome back, aspiring cyberwarriors! In a cyberwar, SCADA and ICS industrial systems can be both a target and a weapon! Although the ongoing tensions between the U.S. and China are often framed as a trade war, Chinese state-sponsored actors have been known to compromise and maintain persistent access to critical
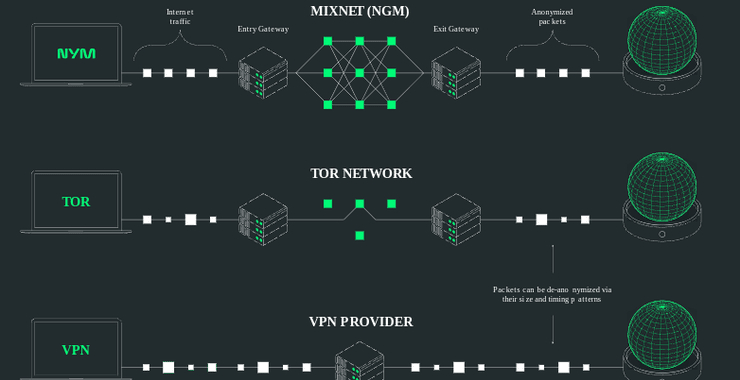
NymVPN. Is This the World’s Most Secure VPN?
Welcome back, my aspiring cyberwarriors! The landscape of digital privacy continues to evolve as surveillance capabilities expand globally. Our digital footprints are continuously tracked, analyzed, and leveraged by various entities. While traditional privacy tools focus on encrypting the content of communications, they often overlook a significant vulnerability: metadata. This

Open-Source Intelligence or OSINT: You Can’t Hide on Telegram!
Welcome back, aspiring cyberwarriors! A lot of people believe that the widely-used social media site, Telegram, offers them anonymity to post confidential information. In this post, we will show you how you can find key information and de-anonymize users on Telegram. Role in the Ukraine/Russia War As
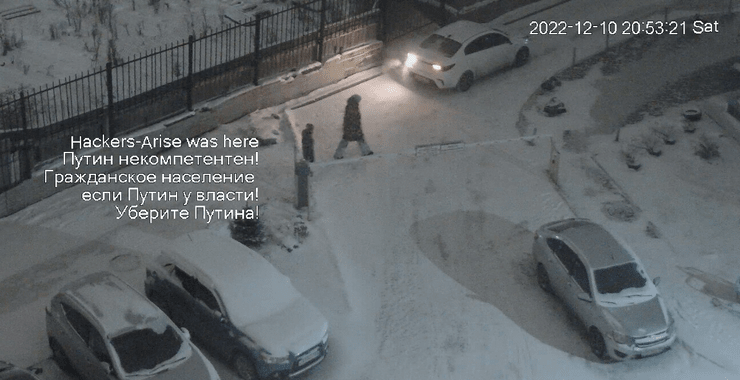
The Default Passwords of Nearly Every IP Camera
Welcome back, my aspiring camera hackers! As you know, at the beginning of the Russian invasion of Ukraine, the Ukrainian Army asked for our assistance to hack IP cameras across Ukraine. This was intended provide surveillance to the Ukraine military and intelligence on Russian troop movements and later to record

OSINT: Automatic Collection Of All Available Information With Intelligence X
Learn how to use IntelligenceX, a powerful OSINT tool for uncovering leaked data, historical web snapshots, and dark web information. This guide walks you through account setup, search techniques, and practical examples to strengthen your cybersecurity investigations.