HACKERS ARISE
Expert-led training in cybersecurity tools and techniques, designed for IT specialists, ethical hackers, security engineers, and students.
We operate on two parallel websites Hackers-Arise.com & Hackers-Arise.net
Live and immersive approach to training ethical hackers
Our instructors are experienced pentesters, forensic investigators, and former college professors. They have trained hackers globally across the multiple military and intelligence agencies. With their broad practical expertise they provide students with practical, high-level skills to tackle the complexities of ethical hacking and excel in the field of cybersecurity.

Top Hacking Articles
CyberWar: The Breach at Avtodor – Inside a Russian Government Infrastructure Network, Part 1
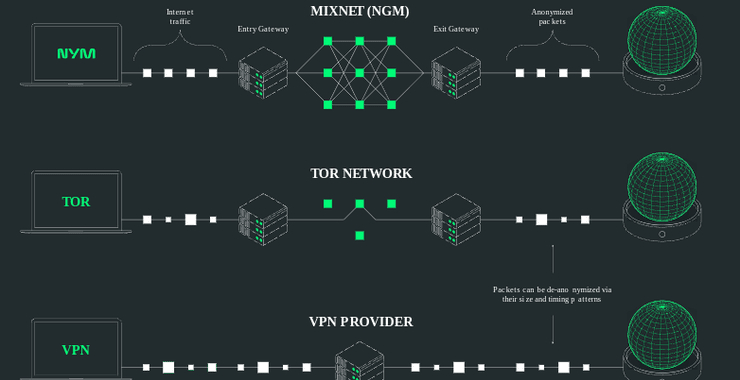
NymVPN Setup & Testing: A Hands-On Walkthrough
Database Hacking: SQLite Essentials and Attack Strategies
Socat: The Advanced Hacker’s Network Tool
SCADA/ICS Hacking and Security: Chinese APT, Volt Typhoon, Has Compromised Numerous Industrial Systems in the US!
OSINT: Automatic Collection Of All Available Information With Intelligence X
Physical Security: Hacking Elevators to Gain Physical Access

HACKING ARTICLES
CATEGORIES
- AI
- Anti-Forensics
- Bitcoin
- Bluetooth
- Bug Bounty
- Cellphones
- Cryptocurrency
- Cryptography Basics
- Cyber Threat Intelligence
- Cybersecurity
- Cyberwar
- Cyberwarrior
- Data Analytics
- Data Dumps
- Defensive Security
- Digital Forensics
- DoS
- Email Dumps
- Exploit Development
- FemtoCell
- GPS
- Hacking
- ICS
- InfoSec
- IoT
- IoT Hacking
- Linux
- Lock Picking
- Malware
- Metasploit
- Network Basics
- Offesnsive Security
- OSINT
- ParamSpider
- Pentesting
- Physical Security
- Python
- Ransomware
- Satellite Hacking
- SCADA Hacking
- Scanner
- Scapy
- Scripting for Hackers
- SDR
- Signals Intelligence
- Spidering
- Stingray
- Ukraine
- Uncategorized
- Vulnerabilities
- White Hat
- Windows

OSINT: Tracking US Spy Planes Surveilling the Mexican Cartels
Welcome back, aspiring cyberwarriors! OSINT has applications in so many fields including pentesting, investigations, cybersecurity, threat intelligence, missing persons, and criminal investigations. OSINT can also help to anticipate future conflicts on the geopolitical stage. Just like the Ukraine/Russia War, we are now seeing indications–via OSINT– that a new storm

Introduction to the IoT/Embedded Linux: The OpenWRT Project
Welcome back, my aspiring cyberwarriors! As you know, the various mobile carriers around the world sell a device they often refer to as a “network extender”. These are actually femtocells or very small cellphone towers. The local cellphone connects to the network extender/femtocell and the signal is then sent across
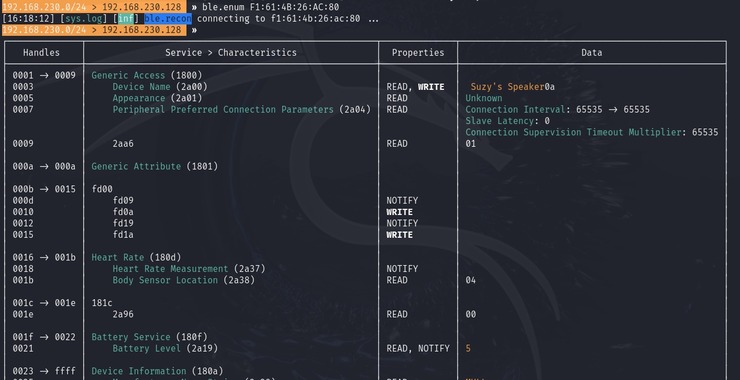
Bluetooth Hacking: Using Bettercap for BLE Reconnaissance and Attacks!
Welcome back, my aspiring cyberwarriors! Bluetooth is the most underappreciated attack vector into all your devices. Nearly all our devices have a bluetooth adapter and connection that is vulnerable to attack. This includes our cellphones, laptops, Smart Home devices, ICS devices and our ubiquitous bluetooth speakers and headsets. If
The Art and Science of Social Engineering in the Age of AI, February 11-13
Many novices to cybersecurity underestimate the importance of social engineering. More experienced hands understand that social engineering is probably the greatest threat to our networks. Many of the most significant hacks in history had a social engineering element including; BlackEnergy3 attack against Ukraine’s power grid Target POS 2016 Presidential

Spray and Succeed: The Hacker’s Guide to Unlocking Weak Passwords
Welcome back, my aspiring cyberwarriors! At the dawn of the Information Age, passwords emerged as the preeminent method for verifying identity. Over half a century later, the password persists as the most common form of digital authentication, securing everything from computers and bank accounts to social media and mobile devices. As
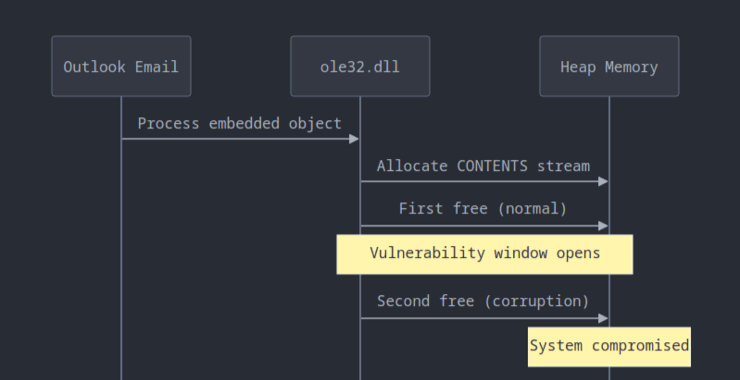
NEW No-Click Critical Vulnerability in Microsoft Windows: CVE-2025-21298
Welcome back, my aspiring cyberwarriors! Over the years, Microsoft Windows operating system, the world’s most widely used OS, has been riddled with security vulnerabilities. As the years have gone by and Microsoft has become more security conscience, the number of critical vulnerabilities has waned, but every so often we