HACKERS ARISE
Expert-led training in cybersecurity tools and techniques, designed for IT specialists, ethical hackers, security engineers, and students.
We operate on two parallel websites Hackers-Arise.com & Hackers-Arise.net
Live and immersive approach to training ethical hackers
Our instructors are experienced pentesters, forensic investigators, and former college professors. They have trained hackers globally across the multiple military and intelligence agencies. With their broad practical expertise they provide students with practical, high-level skills to tackle the complexities of ethical hacking and excel in the field of cybersecurity.

Top Hacking Articles
CyberWar: The Breach at Avtodor – Inside a Russian Government Infrastructure Network, Part 1
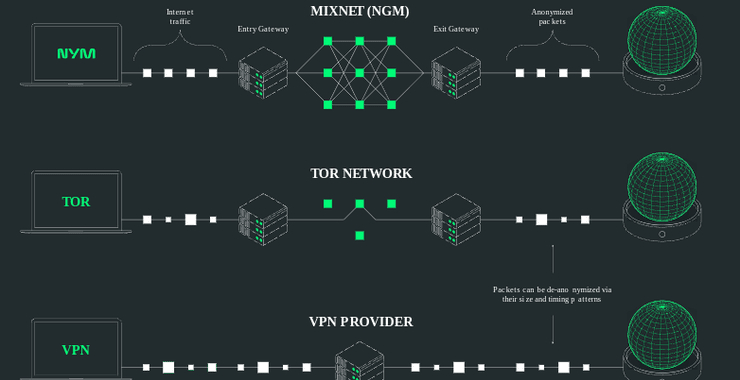
NymVPN Setup & Testing: A Hands-On Walkthrough
Database Hacking: SQLite Essentials and Attack Strategies
Socat: The Advanced Hacker’s Network Tool
SCADA/ICS Hacking and Security: Chinese APT, Volt Typhoon, Has Compromised Numerous Industrial Systems in the US!
OSINT: Automatic Collection Of All Available Information With Intelligence X
Physical Security: Hacking Elevators to Gain Physical Access

HACKING ARTICLES
CATEGORIES
- AI
- Anti-Forensics
- Bitcoin
- Bluetooth
- Bug Bounty
- Cellphones
- Cryptocurrency
- Cryptography Basics
- Cyber Threat Intelligence
- Cybersecurity
- Cyberwar
- Cyberwarrior
- Data Analytics
- Data Dumps
- Defensive Security
- Digital Forensics
- DoS
- Email Dumps
- Exploit Development
- FemtoCell
- GPS
- Hacking
- ICS
- InfoSec
- IoT
- IoT Hacking
- Linux
- Lock Picking
- Malware
- Metasploit
- Network Basics
- Offesnsive Security
- OSINT
- ParamSpider
- Pentesting
- Physical Security
- Python
- Ransomware
- Satellite Hacking
- SCADA Hacking
- Scanner
- Scapy
- Scripting for Hackers
- SDR
- Signals Intelligence
- Spidering
- Stingray
- Ukraine
- Uncategorized
- Vulnerabilities
- White Hat
- Windows

Physical Security: Hacking Elevators to Gain Physical Access
Welcome back, my aspiring cyberwarriors! In the realm of physical security and red team operations, elevators present an often-overlooked but strategically important vector. While they may seem like mundane infrastructure, elevators are embedded with layers of logic, legacy systems, and mechanical overrides that can be leveraged or manipulated—given the right

SDR (Signals Intelligence) for Hackers: Soon, all Cellphones will be Connected by Satellites
Welcome back, my aspiring cyberwarriors! In earlier posts here, we have described hacking satellite communication systems. While many might see that type of hacking as very advanced and maybe a bit esoteric, new technologies are about to make satellite communication ubiquitous for everyone with a cellphone. We are on
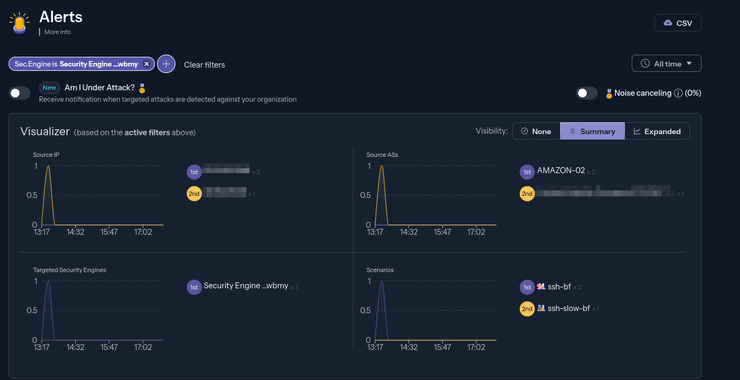
Cyber Threat Intelligence (CTI) and Network Defenses: Getting Started with CrowdSec
Welcome back, aspiring cyberwarriors! In the ever-evolving landscape of cybersecurity, new tools and approaches are constantly emerging to combat the growing sophistication of cyber threats. One such innovative solution is CrowdSec, a free and open-source security automation tool that leverages the power of crowdsourcing to detect and mitigate cyber

The CyberWarrior Handbook, Part 1
Welcome back, my cyberwarriors! In this series, we will detail how an individual or small group of cyberwarriors can impact global geopolitics. The knowledge and tools that YOU hold are a superpower that can change history. Use it wisely. To begin this discussion, let’s look at
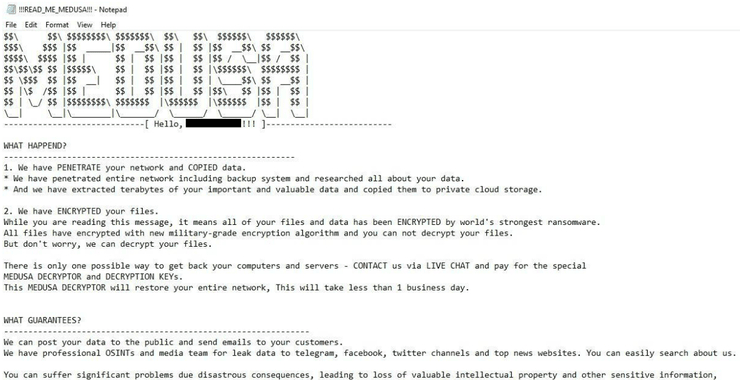
The Medusa Ransomware Threat: Anatomy of a Cybercrime Operation
Welcome back, aspiring cyberwarriors! In Greek mythology, Medusa was once a beautiful woman until Athena’s curse transformed her into a winged creature with a head full of snakes. She is seen as both a monster and a protector, possessing the power to turn anyone who gazes upon her face to
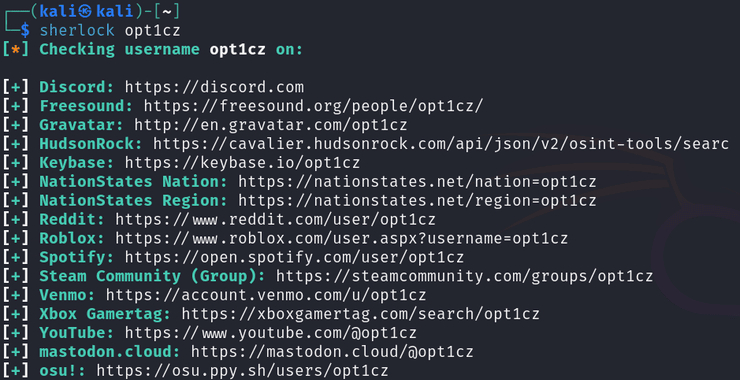
Open-Source Intelligence(OSINT): Sherlock – The Ultimate Username Enumeration Tool
Welcome back, aspiring OSINT investigators! Social media platforms hold a wealth of personal and professional information, making them valuable for reconnaissance in penetration testing and cyberwarfare operations. Sherlock is a lightweight yet powerful tool designed to search for social media profiles using a username. In this article, we’ll guide