HACKERS ARISE
Expert-led training in cybersecurity tools and techniques, designed for IT specialists, ethical hackers, security engineers, and students.
We operate on two parallel websites Hackers-Arise.com & Hackers-Arise.net
Live and immersive approach to training ethical hackers
Our instructors are experienced pentesters, forensic investigators, and former college professors. They have trained hackers globally across the multiple military and intelligence agencies. With their broad practical expertise they provide students with practical, high-level skills to tackle the complexities of ethical hacking and excel in the field of cybersecurity.

Top Hacking Articles
CyberWar: The Breach at Avtodor – Inside a Russian Government Infrastructure Network, Part 1
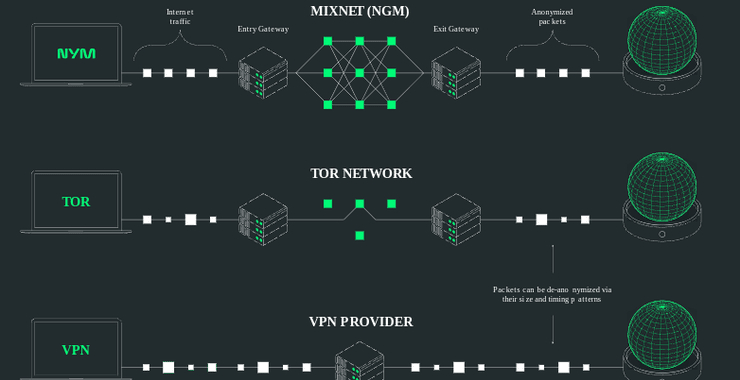
NymVPN Setup & Testing: A Hands-On Walkthrough
Database Hacking: SQLite Essentials and Attack Strategies
Socat: The Advanced Hacker’s Network Tool
SCADA/ICS Hacking and Security: Chinese APT, Volt Typhoon, Has Compromised Numerous Industrial Systems in the US!
OSINT: Automatic Collection Of All Available Information With Intelligence X
Physical Security: Hacking Elevators to Gain Physical Access

HACKING ARTICLES
CATEGORIES
- AI
- Anti-Forensics
- Bitcoin
- Bluetooth
- Bug Bounty
- Cellphones
- Cryptocurrency
- Cryptography Basics
- Cyber Threat Intelligence
- Cybersecurity
- Cyberwar
- Cyberwarrior
- Data Analytics
- Data Dumps
- Defensive Security
- Digital Forensics
- DoS
- Email Dumps
- Exploit Development
- FemtoCell
- GPS
- Hacking
- ICS
- InfoSec
- IoT
- IoT Hacking
- Linux
- Lock Picking
- Malware
- Metasploit
- Network Basics
- Offesnsive Security
- OSINT
- ParamSpider
- Pentesting
- Physical Security
- Python
- Ransomware
- Satellite Hacking
- SCADA Hacking
- Scanner
- Scapy
- Scripting for Hackers
- SDR
- Signals Intelligence
- Spidering
- Stingray
- Ukraine
- Uncategorized
- Vulnerabilities
- White Hat
- Windows
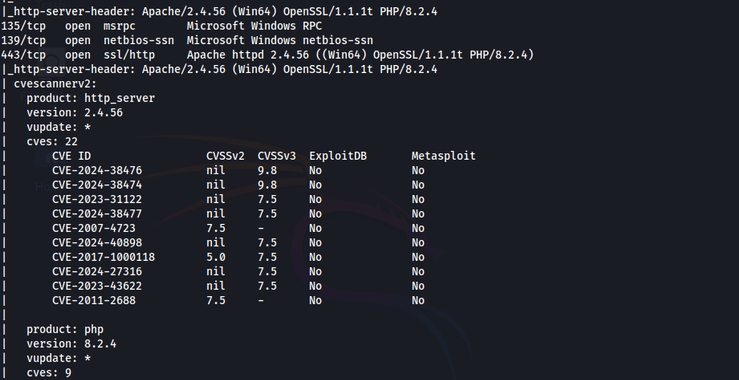
Vulnerability Scanning: Automatic Search For Known CVEs With CVEScannerV2
Welcome back, aspiring cyberwarriors! During reconnaissance, our goal is to identify vulnerable services within our target’s network. To streamline this process, CVEScannerV2 was developed – a powerful Nmap script that bridges the gap between network scanning and vulnerability assessment. This tool enhances the capabilities of the widely-used Nmap scanner,

Why YOU Should Study Software Defined Radio (Signals Intelligence) for Hackers!
Hacking radio signals (RF) IS the leading edge of cybersecurity! So many applications in our modern life use radio frequency elements that it is hard to list them all. For instance, consider the following list: Automobile and vehicle access and monitoring Mouse and keyboards Cellphone Signals Remote control Telemetry

Vagrant: Building Secure Testing Environments
Welcome back, aspiring cyberwarriors! Creating and managing virtual machines has traditionally been a tedious and time-consuming process. System administrators and developers often struggled with the challenges of replicating virtual environments across different servers, a task that becomes exponentially more complex when dealing with multiple VMs. This complexity not only
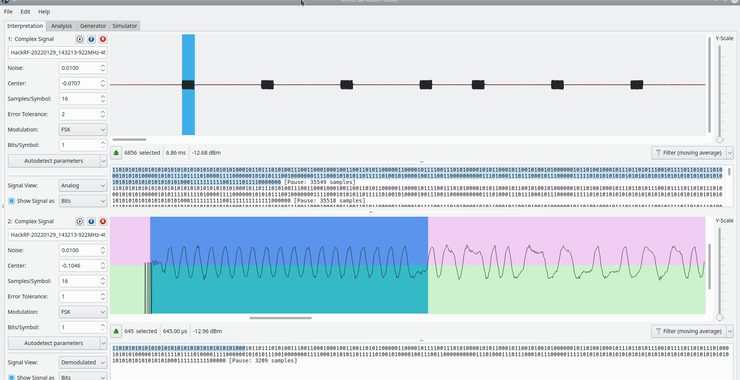
Hackers-Arise Announces a New Program! SDR (Signals Intelligence) for Hackers!
Hackers-Arise is so excited to offer this new program and career path! Software Defined Radio and specifically, Signals Intelligence, is the cutting edge of cybersecurity! So many have asked for a specific career path in this field that we responded! If you a newcomer to cybersecurity or
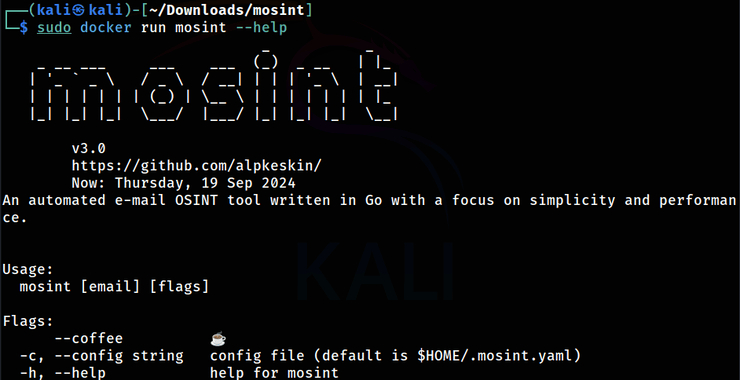
Open Source Intelligence (OSINT): The Versatile Email Address Search Tool
Welcome back, aspiring cyberwarriors and OSINT investigators! In our digital age, email addresses have become the keys to our online identities. They’re used for everything from social media accounts to financial services, making them prime targets for hackers. As OSINT investigators, pentesters, and hackers, we often need to determine if

Cyberwar Mission #3: Using QRCodes in Phishing and Social Media Attacks
Welcome back, aspiring cyberwarriors. In this article, one of our fighters in Ukraine (Sierra) demonstrates how they use social engineering to turn Russian tactics against them. In each new article here, we delve into the cyberwarrior wisdom of Master OTW and its application in cyber warfare. In this