HACKERS ARISE
Expert-led training in cybersecurity tools and techniques, designed for IT specialists, ethical hackers, security engineers, and students.
We operate on two parallel websites Hackers-Arise.com & Hackers-Arise.net
Live and immersive approach to training ethical hackers
Our instructors are experienced pentesters, forensic investigators, and former college professors. They have trained hackers globally across the multiple military and intelligence agencies. With their broad practical expertise they provide students with practical, high-level skills to tackle the complexities of ethical hacking and excel in the field of cybersecurity.

Top Hacking Articles
Ukraine/Russia Cyber War! Using SQLi Against Russian Websites, Part 2
Linux Basics for Hackers: Building a Router with nftables
Kubernetes Hacking: Attacking Kubernetes Clusters Using The Kubelet API
Ukraine/Russia CyberWar! Targeting Russian Websites with SQL Injection
VPN Vulnerabilities You Should Know About in 2025
Linux Basics for Hackers, the Make Command: Compiling and Installing Software from Source in Linux
Python Basics for Hackers, Part 6: Decoding an Encrypted Message with Frequency Analysis (Cryptanalysis)

HACKING ARTICLES
CATEGORIES
- AI
- Anti-Forensics
- Bitcoin
- Bluetooth
- Bug Bounty
- Cellphones
- Cryptocurrency
- Cryptography Basics
- Cyber Threat Intelligence
- Cybersecurity
- Cyberwar
- Cyberwarrior
- Data Analytics
- Data Dumps
- Defensive Security
- Digital Forensics
- DoS
- Email Dumps
- Exploit Development
- FemtoCell
- GPS
- Hacking
- ICS
- InfoSec
- IoT
- IoT Hacking
- Linux
- Lock Picking
- Malware
- Metasploit
- Network Basics
- Offesnsive Security
- OSINT
- ParamSpider
- Pentesting
- Physical Security
- Python
- Ransomware
- Satellite Hacking
- SCADA Hacking
- Scanner
- Scapy
- Scripting for Hackers
- SDR
- Signals Intelligence
- Spidering
- Stingray
- Ukraine
- Uncategorized
- Vulnerabilities
- White Hat
- Windows
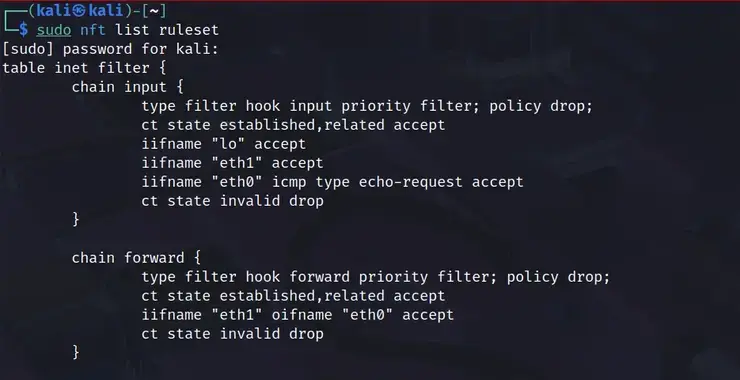
Linux Basics for Hackers: Building a Router with nftables
Welcome back, aspiring cyberwarriors! As you know, traditional hardware routers can be expensive, inflexible, and often come with proprietary firmware that limits your control. By leveraging the power of Linux and nftables, you can create a customized routing solution that gives you complete control over your network traffic, security policies,
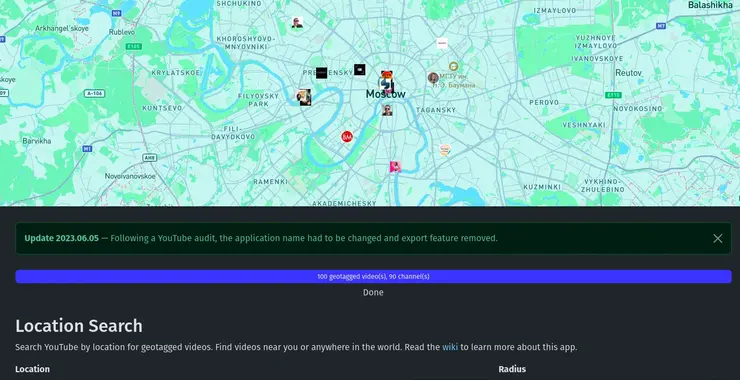
Open-Source Intelligence (OSINT): Unmasking YouTube with OSINT Tools!
Welcome back, aspiring cyberwarriors! In our digital investigations, we often need to extract valuable intelligence from video content. This might include identifying locations, uncovering connections between individuals, finding deleted content, or simply gathering information that someone has inadvertently shared on camera. It is critical that we know how to effectively
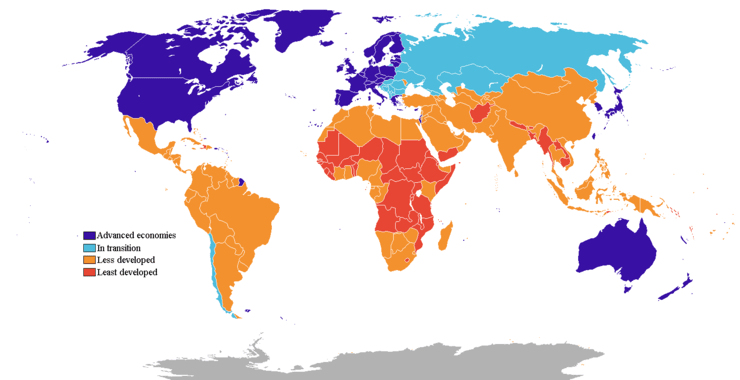
50% off Subscriber and Subscriber Pro for those in non-industrialized Nations!
We recognize that incomes vary dramatically from one nation to the next and we don’t want to exclude anyone from the best cybersecurity training anywhere! If you live in a non-industrialized nation, you can become a Subscriber or Subscriber Pro at 50% off! If you live in a country other

Ukraine/Russia Cyber War! Using SQLi Against Russian Websites, Part 2
Hello cyberwarriors! This is Overwatch from Ukraine again! In the first segment of this series, we walked through different modifications of SQLMap payloads. Today, we’re continuing our SQL injection series, but will focus on automating the scanning process to save time and make it easier to work with larger sets

Mobile Hacking: How the Mexican Drug Cartels Built their Own Cellular Infrastructure to Avoid Surveillance
Welcome back, my aspiring cyberwarriors! Mobile hacking can take many forms. It can entail any of the following; (1) a hack against a singular phone such Pegasus and many other IoS and Android malware, (2) an attack against the mobile infrastructure such as SS7 (Chinese hackers have recently

Kubernetes Hacking: Attacking Kubernetes Clusters Using The Kubelet API
Welcome back, aspiring cyberwarriors! In this article, we will explore how to search for and exploit vulnerabilities in the Kubernetes Kubelet API, focusing on its default unauthenticated access. Kubernetes is a portable, extensible, open-source platform for managing containerized workloads and services. When you deploy Kubernetes, you get